Recently PCMDX received a call from a business who’s bank account had been compromised. Someone, using legitimate information, was able to gain access to the account and make transfers from the account to another account, and also made wire transfers to a third party.
The business had been told by the bank that their network had been hacked and that they should seek some help in securing their network, which is why they contacted PCMDX. We focus providing network support for small businesses that have less than 15 computers, and one of our specialties is cybersecurity and compliance.
Although how the actors (the term used for the “bad guys” since they are “acting” as a legitimate party) were able to get the necessary information is still under investigation, it’s likely that it was given to them by one of the company officers via e-mail.
We recently received a scam e-mail and we’d like to share it with you so that you can learn how to determine if it’s a legitimate e-mail or not. Please note: If you’re not sure if the e-mail is legitimate, call the sender and ask them if they sent it, even if it passes all of the tests. It’s better to be safe and verify authenticity than take a chance.
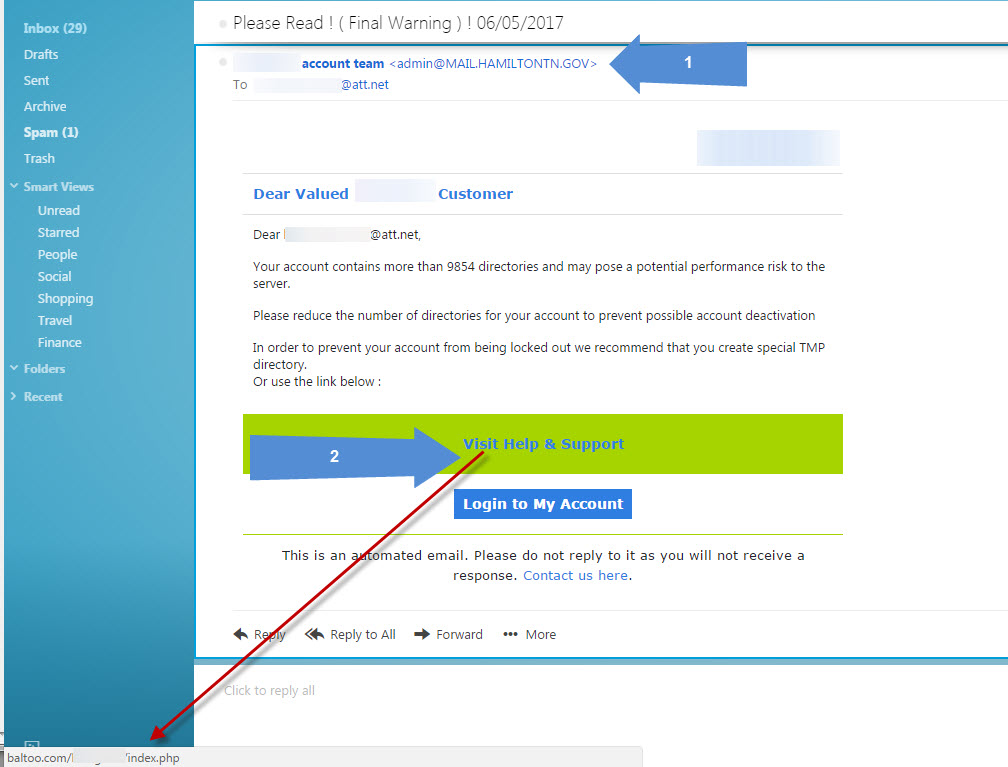
Here’s a screenshot of the e-mail we received, along with some notes (Click on the image for a full size view). We blurred out information that is not relevant.
Let’s begin at the top. The subject line “Please Read! (Final Warning) | 06/05/2017” sounds pretty threatening and will get your attention right away. But it doesn’t indicate who it’s from or what it’s about.
If you look at Blue Arrow 1, you’ll see that it’s from “ACME account team”, followed by the e-mail address of “admin@MAIL.HAMILTONTN.GOV”. (We’re going to use ACME as the alias for the name of the company). So here you have two major clues that this is a scam. First, the words ACME account team. Any legitimate company will list themselves as ACME Account Team, with all words capitalized. This is a major clue that this e-mail did not originate in the US (most scam e-mails are from overseas, where grammar is poor).
Our next clue is the e-mail address. Although “admin” is legitimate, MAIL.HAMILTONTN.GOV is not. That’s an e-mail server for the city of Hamilton, Tennessee. It has a .gov domain ending, which can only be assigned to government entities, such as cities, counties, states and the federal government. Why would ACME have this domain? If it were a legitimate e-mail from ACME, it would end with something like ACME.com or ACME.net, not a .gov domain.
The body of the e-mail is actually very good, at least when it comes to scam e-mails. It’s convincing, it has information in it that the typical person would consider to be legitimate. However, as we get to the bottom, some red flags appear.
When you hover over a link (and the Blue Arrow 2 is pointing to two links, “Visit Help and Support” and “Login to My Account”), the bottom part of your browser, known as the status bar, will display the link that it’s pointing to, which we’re using the red arrow to point to. In other words, when you click on the link, it’s taking you to the web site that is showing in the status bar.
This particular link is pointing to baltoo.com/ACME/index.php . This should immediately sound an alarm with the person reading the e-mail. The company that is sending this is ACME, but the domain it’s pointing to (the first part of the web address is always the domain) is baltoo.com . Anything after the domain name is irrelevant, since that’s just the directory and folder inside the server it’s pointing to, and you can name that anything you want. When you hover over the link, it should point to the company you’re trying to go to. So it should read acme.com/Acme/index.php.
Once you click on the link, one of two things will happen. Either you will be shown a very convincing site that is asking for your user name and password, or you will end up on poisoned site that will infect your computer with malware, such as a virus, a Trojan, or ransomware. If it’s the former, you’ll enter the user name and password, and within minutes the actors will have gained access to your site (as they wanted to in this case), or perhaps gained information such as name, address, social security number, date of birth, etc. (under the guise of “verifying your identity”).
Recent studies have shown that firewalls, anti-virus programs, and other security software and hardware, although still crucial in preventing attacks, need to be supplemented by training of staff so they know what they should look for. (That page also has a quiz you can take to see how much you know about phishing attacks – we scored 10/10. How’s your score?).
Our companion site, Don’t Become Another Target lists dozens of examples of how companies, some billion dollar plus companies, were compromised not by technology, but by social engineering. In other words, a con job either via e-mail or via phone. Adequate training would have prevented many of the attacks.
If you’re a small business that doesn’t have an IT department, but would like IT level support, contact PCMDX today. We’ll take care of your computer network and cybersecurity needs so you can take care of your business. And don’t wait until you’ve been compromised. The cleanup is much costlier than the prevention.